Life Cycle Of Applet And Security Concerns
What is information security lifecycle management? Change management software development life cycle Applet in java
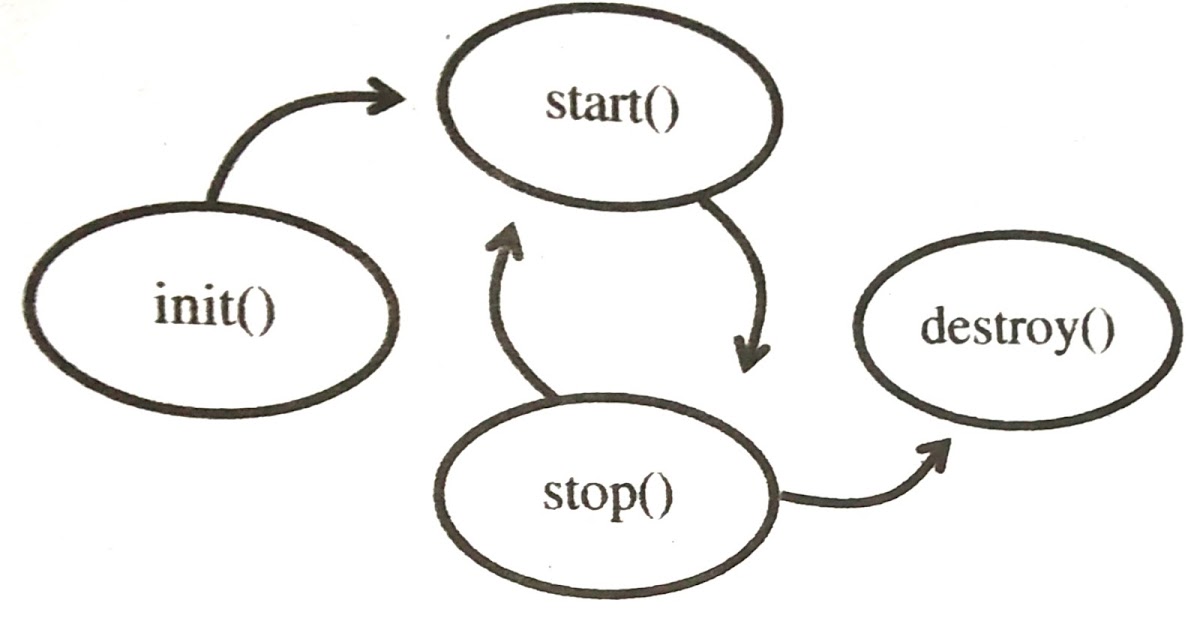
Applet Life Cycle in Java - Javatpoint
Applet life cycle in java What are the steps of the information security program lifecycle Java processing: life cycle of a papplet
Information life cycle diagram
Protección de datos en todo su ciclo de vidaApplet java cycle life studytonight simple Secure software development life cycleApplet applets lifecycle void oureducation.
Applet life cycle in javaLife cycle of java applet Write a short note on life cycle of applet.Pdf import java.applet.applet.

Applet life cycle
Life cycle of an appletLife cycle of java applet Applets in javaComputer revolution (www.comrevo.com): life cycle of applet.
Life cycle of appletHow your employees open doors for hackers Applet life cycle?Fraud, aml & security intelligence.

Applet cycle java
Applet cycle life states includeSecure software development life cycle (sdlc) introduction Security information cycle policy life ppt powerpoint presentationInformation security life cycle [10, p. 123].
Strategic planning: security program life cycleApplet life cycle diagram revolution computer initialized Applet javatpointSecure system development life cycle (secsdlc).

Cycle applet life java programming
Introduction to applets & applet life cycleSoftware development life cycle sdlc atories Systems development life cycle (sdlc)-information security, computerThe information security lifecycle.
Applet cycle life stateUltimate guide to system development life cycle Building a 5-phase cybersecurity lifecycle framework for your businessLife cycle applet state.

Figure 1 from a life cycle approach to information security policy for
.
.

PPT - IS 380 PowerPoint Presentation, free download - ID:2824350

Applets in Java | Core Java Tutorial | Studytonight

Applet in JAVA | Core JAVA Notes Describing Applets Life Cycle in pdf

Applet life cycle? | Computers Professor

Secure Software Development Life Cycle

Figure 1 from A Life Cycle Approach to Information Security Policy for

Strategic Planning: Security Program Life Cycle